Barriers Materials and Construction
Walls
Partition Design
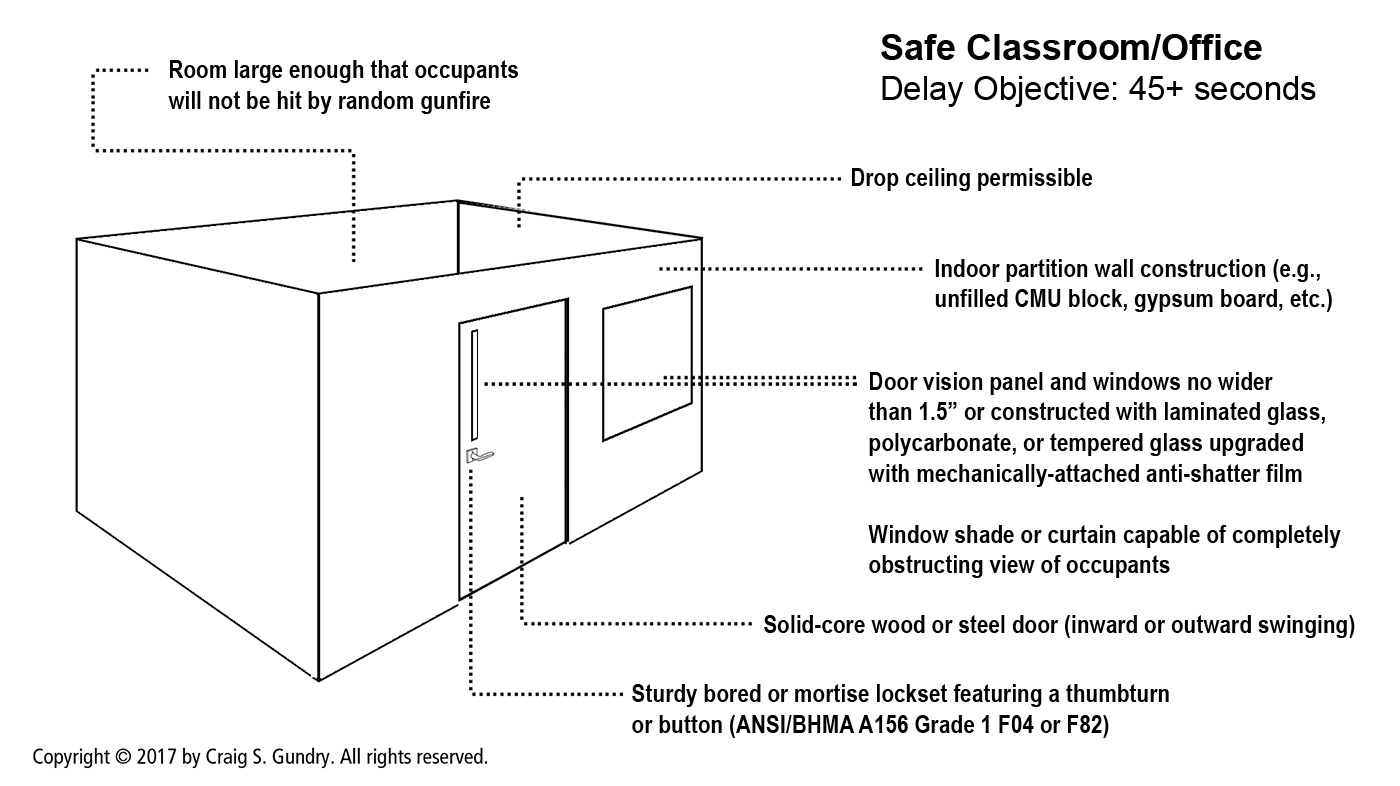
Ideally, walls defining protective layers (e.g., secure lobbies, safe rooms, etc.) should be designed as full partitions extending floor-to-ceiling to minimize opportunity for easy access through drop ceilings. In high-risk situations or design applications where the intervention of security or police forces is expectedly delayed, full partition walls should be a basic requirement.
In low-risk applications and situations where the primary design objective is to simply frustrate adversary access, drop ceilings may be a justifiable compromise. As described in Part One of this article, armed attackers most often use visually-obvious portals (e.g., doors and windows) as their main pathways for movement. Although entry through drop ceilings is certainly possible, our research has not revealed any active shooter attacks to date where drop ceilings were exploited as a means of accessing people located in locked rooms.
Intrusion Resistance of Walls
In alignment with the principles of balanced protection, walls should ideally resist forced intrusion with similar delay times as doors, locks, and windows. In many commercial and academic facilities, walls protecting rooms commonly designated for use as safe rooms (e.g., offices, conference rooms, classrooms, etc.) are often secured by little more than two layers of gypsum board on wooden studs. Some sources suggest two-layered drywall partitions can be penetrated in 60 seconds by an adversary without use of equipment and 30 seconds with the assistance of hand tools.[1] Despite the poor performance of gypsum board walls, they may be a justifiable compromise in some situations, considering the rare frequency of active shooter attacks where walls have been used as a point of entry into locked rooms. In low-risk applications or situations where budget limits retrofit options, we rarely recommend replacement or upgrade of existing drywall.
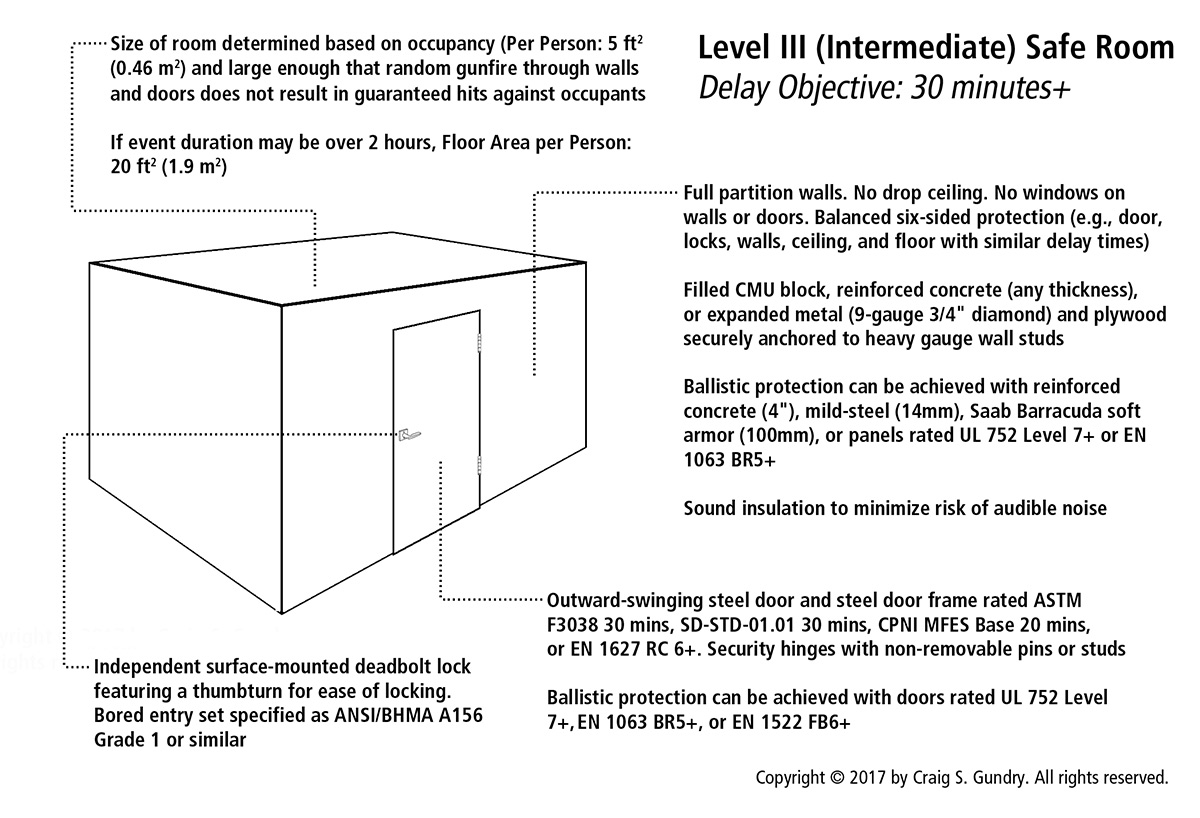
In medium-high risk applications and safe room designs with delay time objectives over 45 seconds, walls should be constructed using intrusion-resistant materials. Some options for protective wall construction include reinforced concrete, filled masonry block, expanded metal mesh, and polycarbonate-composite wall panels.
Reinforced concrete walls provide the best delay time performance against adversaries using limited toolsets. According to tests documented by Sandia, 4-inches of reinforced concrete with No. 5 rebar on 6-inch centers will provide approximately 4.7 minutes of delay against penetration with hand tools (including saw).[2] If our threat definition is an adversary relying solely on firearm penetration and blunt object impact, reinforced concrete of any dimensions will provide almost indefinite delay.
Contrary to what many assume, unfilled concrete masonry unit (CMU) block walls provide minimal delay against forced entry and only slightly better performance than drywall against some methods of penetration. According to data published in the Barrier Technology Handbook, the mean delay time for penetrating an unfilled CMU block wall is only 36 seconds by the use of a sledgehammer.[3] Unfilled CMU block walls are also susceptible to damage by rifle projectiles and may crumble when struck repeatedly by gunfire.[4] For better performance in delaying forced entry, CMU block walls should be fully grouted and reinforced with rebar. According to tests documented by Sandia, filled 8-inch CMU walls with No. 5 rebar on 14-inch centers provide approximately 1.4 minutes of delay against penetration with hand tools.[5]
Supplementing exterior drywall layers with a securely attached inner layer of expanded metal mesh is one of the most common methods of retrofitting existing walls for improved resistance against forced entry. Expanded steel constructed of 9-gauge 3/4-inch diamond mesh is a common material specification for this purpose. In this type of wall design, the expanded metal mesh is installed on the inside of the protected room and secured to wall studs by using deep screws and fasteners specially designed for this purpose. The expanded metal barrier layer is then overlaid with gypsum board or plywood. According to Sandia, a wall constructed of two layers of 3/4-inch plywood, two layers of gypsum board, and an expanded metal mesh interlayer can provide as much as 6.5 minutes of delay against penetration with hand tools.[6] Despite the popularity of 9-gauge material as a safe room design specification, money can often be saved by using a lighter mesh without compromising performance. If the threat definition is an adversary equipped solely with a firearm, static and dynamic impact force will be the main mechanisms of penetration, and overall strength of the fastening system will be more important than thickness of the metal fabric.
Several manufacturers currently offer polycarbonate composite wall panel products marketed for security applications. Most products of this type are composed of a thin polycarbonate layer (0.08-0.125 inch) bonded to gypsum or cement board. Manufacturers of polycarbonate composite wall systems are generally cautious about describing the capabilities of these products. Most manufacturers only cite single-impact static force tests up to 3,200 ft-lbf. When addressing impact resistance, one manufacturer cites testing under ASTM D2394-83. However, ASTM D2394 relates to the performance of finish flooring against abrasion, friction, and indentation and offers no insight on protective value. Although the concept of these products is very appealing, their use in performance-based protective design is discouraged in the absence of more reliable and promising test data.
Ballistic Resistance of Walls
One of the best references for specifying construction of bullet-resistant walls is U.S. DoD UFC 4-023-07 (Design to Resist Direct Fire Weapon Effects). [7] According to UFC 4-023-07, walls constructed of 4-inches reinforced concrete, 8-inch filled CMU block (grouted full), and 8-inches of brick will resist penetration by 7.62x51mm ammunition.[8] UFC 4-023-07 also provides ballistic resistance specifications for steel plate barriers. However, at the thicknesses specified by DoD, steel is not a practical option in most indoor design situations due to structural load and construction challenges.
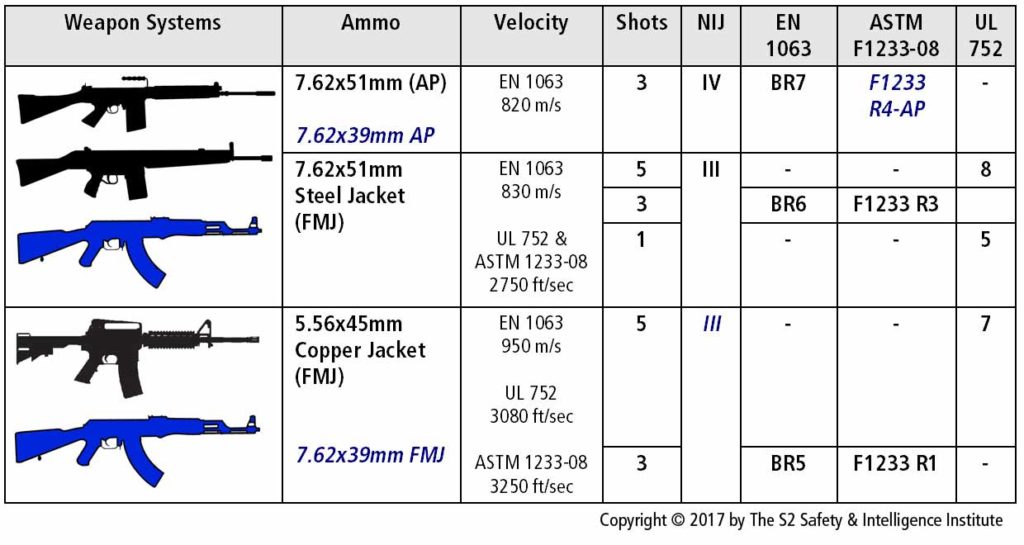
A number of manufacturers also produce fiberglass wall panels rated for ballistic resistance under UL 752, ASTM F1233-08, and EN 1063.[9][10][11] Minimum specifications for protection against military small arms (5.56mm) would be UL 752 Level 7, F1233 R1, or EN 1063 BR5. More conservative specifications for 7.62x51mm include UL 752 Level 8, F1233 R3, and EN 1063 BR6.
In addition to fiberglass panels, Saab’s Barracuda Soft Armor offers an easy method for upgrading hollow walls into bullet-resistant barriers. The Barracuda Soft Armor is designed as 13mm ceramic balls used as infilling between wall boards. Thickness of the armor-filled wall cavity determines its ballistic resistance capabilities. According to Saab’s product literature, 100mm of Barracuda pellets is the technically-estimated specification for protection against 7.62mm FMJ projectiles and 120mm of Barracuda armor has been technically-verified as ~99% effective in resisting 7.62mm armor piercing ammunition.[12] Although Saab does not cite tested ratings according to UL 752 or EN 1063, 125mm Barracuda armor has been certified as STANAG 4569 Level 3 (7.62x54R and 7.62x51AP).[13]
Doors
If the risk level and design approach requires door systems rated for tested delay times, doors certified under SD-STD-01.01, ASTM F3038-14, CPNI MFES, LPS 1175 have been tested against a variety of forced entry methods and often exceed requirements for protection during short-duration armed events. If the threat definition identifies an adversary solely employing firearms and expedient tools, any door certified under SD-STD-01.01, ASTM F3038-14, CPNI MFES, or LPS 1175 will likely far exceed performance as suggested by its certified delay time rating.
Considering the cost of security doors and the number of rooms often desired for availability as safe rooms during armed attacks, many organizations do not have the budget or risk justification required for implementing security doors rated under forced entry standards. In this situation, specification may require choosing commercial door hardware with security features adequate to accomplish the design objective or retrofitting existing doors with cost-consciously selected upgrades for maximum benefit.
Intrusion Resistance of Doors
As a general rule, outward-swinging doors provide the best protection against exterior ramming force due to resistance of the rebate within the frame. Additionally, adversaries attempting to pull open locked outward-swinging doors without the aid of tools are at a great mechanical disadvantage. If rooms earmarked as potential safe rooms feature existing inward-swinging doors, door hardware (e.g., locks, strikes, and frames) should be carefully specified to ensure adequate resistance against ramming force.
Most security doors certified under forced entry standards are constructed of steel. However, indoor rooms potentially earmarked for use as safe rooms in office and academic facilities are often equipped with solid core wood or solid wooden doors. Solid core doors are constructed with a composite wood core and overlaid with hardwood veneer for aesthetic appearance. The times required to penetrate solid core and solid wooden doors using methods likely to be encountered during active shooter attacks has never been published. Considering the materials involved, solid wooden doors are preferable to solid core doors. Nevertheless, for application against a gunman employing impact force without additional tools, solid door leafs (regardless of construction) are unlikely to be the point of failure when compared to the potential vulnerability of locks, strikes, wooden frames, and vision panels.
Doors featuring glass vision panels are often highly vulnerable to forced entry. Tempered safety glass panels only provide about 10 seconds of delay against a gunman. Once broken, the intruder can simply reach through the window and manipulate the inner door handle or lock to gain entry. To limit this vulnerability, vision panels should be no wider than 1.5″ (3.8 cm) or constructed of intrusion-resistant glazing such as laminated glass, polycarbonate, or reinforced with anti-shatter film. If the delay time objective exceeds a few minutes, vision panels should be avoided completely. Although there are door sets rated under LPS 1175 and ASTM forced entry standards which feature vision panels, it is generally impractical to upgrade or replace vision panels on commercial doors to sufficiently achieve more than a few minutes of delay.
In situations where performance objectives exceed 15 minutes of delay or adversaries are expected to possess a diverse toolset, security hinges should be installed on safe room doors to reduce the risk of hinge pin removal or cutting. Security hinges with dog bolts can also aid in reducing vulnerability to some tool-aided methods of entry. All door frames on safe rooms (regardless of application) should be constructed of steel.
If the budget and risk level justify installation of doors rated under security standards, specifications for a basic level of forced entry resistance include EN 1627 RC4+ and LPS 1175 SR2+. For higher levels of protection, specifications using ASTM 3038, SD-STD-01.01, and CPNI MFES provide a more reliable basis for delay time performance.
Ballistic Resistance of Doors
Although the author is not aware of any comprehensive published ballistic tests of common commercial door products, it is safe to assume most commercial steel, wooden, and solid core doors are vulnerable to penetration by military small arms. If safe room design objectives require ballistic protection, doors rated UL 752 level 7+ or EN 1522 FB5+ should be specified. Additionally, all doors rated under SD-STD-01.01 have been tested against penetration by 5.56mm, 7.62x51mm, and 12-gauge shotgun.
Locks
Simplified Locking
As a prerequisite criterion, all mechanical locks on safe room doors should feature thumbturns for ease of locking under stress. In several previous active shooter attacks, critical doors on rooms where people were seeking refuge remained unlocked during the event owing to absence of a key.[14] Additionally, good preparation for active shooter events should anticipate the effects of the Sympathetic Nervous System (SNS) on employee response. During high stress events, the SNS is often activated with impairing effects on cognitive function and fine motor coordination. These negative effects of the SNS can interfere with even simple tasks such as locating and manipulating keys.
Ironically, considering the history of active shooter attacks in American schools, locks classified by ANSI as “classroom function” (mortise F05 and bored F84) are perhaps the worst choice for safe room applications and should be avoided when possible. Classroom function locks are only lockable by a key from the outer side of the door. Not only do these locks require a key, but they also require the occupant to open the door and reach into the hallway to secure the lock.
Intrusion Resistance of Locks
For protection against entry by buttstock impact and kicking, all lever and knob sets on safe room doors should ideally be rated ANSI/BHMA A156 Grade 1 or have a minimum Security Grade of 4 under EN 12209.[15][16] Mechanical locks rated ANSI/BHMA Grade 1 and EN 12209 Security Grade 4+ have been successfully evaluated under a variety of static force and torque tests.
If the design objective is to simply frustrate access by non-committed adversaries, doors secured only by ANSI/BHMA Grade 1 or EN 12209 Security Grade 4+ latch locksets may be sufficient. However, if the design objective is to delay penetration by a committed adversary or the threat definition includes a diverse range of entry tools, locksets should feature a deadbolt or augmented by the installation of an independent deadbolt lock. In medium security applications, single-point deadbolt locks are often adequate. In situations where greater delay times are required or adversaries are expected to employ improved toolsets for entry, multi-point deadbolt systems provide the best protection.
Surface-mounted deadbolt locks are generally superior to mortise and bored locks in resisting forced entry. Surface-mounted deadbolt locks can incorporate bolts unconstrained by the thickness of doors and require the adversary to entirely penetrate the door leaf to access the lock.[17] Surface-mounted deadbolt systems are also less vulnerable to prying due to the increased force necessary to lever the entire door frame.
Many surface-mounted deadbolt systems designed for high security applications feature auto-bolting locks. Auto-bolting systems lock automatically when the door is closed and often disengage automatically when the inside handle is operated for exit. Manually-bolted surface-mounted deadbolts require a manual unlocking operation to permit exit. Building and life safety codes should be reviewed to ensure permissibility before installing manually-bolted surface-mounted locks. Although some jurisdictions prohibit use of manually-bolted locks on school classroom doors, manually-bolted surface-mounted deadbolts are fully permissible in most locations except when installed on egress doors. This generally addresses most concerns regarding upgrading offices, conference rooms, and similar locations as safe rooms. Under International Building Code 2012, surface-mounted deadbolts are also permissible on egress doors in certain circumstances. For instance, IBC 1008.1.9.4 (Bolt Locks) contains a rule exception for use of surface-mounted deadbolt locks on egress doors with occupant loads of less than 50 persons in Group B (Business Group), F (Factory), and S (Storage) occupancies.[18]
Ballistic Resistance of Locks
Another issue to consider in safe room design is the vulnerability of door hardware to ballistic damage. Although forced entry by ballistic attack against locks and hinges has been rare during active shooter events, a number of incidents have occurred where adversaries forcibly entered/or attempted to penetrate rooms by destroying door locks with gunfire.[19]
The only product certification standard that specifically addresses door locks as a component of ballistic testing is the U.S. Department of State’s SD-STD-01.01.[20] Withstanding a handful of exceptions, most lock manufacturers do not subject standard products to ballistic testing in accordance with protocols such as UL 752 and EN 1522.
Furthermore, Sandia National Laboratories and similar research institutions have not published empirical test data to assist in estimating the ballistic vulnerability of locks commonly used in academic and commercial facilities. In the absence of definitive references, perhaps one of the best sources we have for estimating the performance of common door locks against firearm-aided penetration is the television program MythBusters Special 9 “Shootin’ Locks.”[21] Although the sample size tested by MythBusters was very small, the results of testing suggest that bored deadbolt locks are resistant to single-shot penetration by handgun calibers (9mm and .357 magnum) and vulnerable to defeat by high powered rifle (.30-06 cal.) and 12-ga. shotgun slugs. U.S. Army field manual FM 3-21 also states that a shotgun is effective at defeating door locks.[22] Regarding rifle calibers, FM 3-21 somewhat conflicts with the Mythbusters findings by stating that 5.56mm and 7.62mm “have proved to be virtually ineffective for breaching.”[23] From these limited sources, it’s reasonable to assume most locks will be resistant to critical damage by handguns, definitely vulnerable to shotguns, and susceptible to some rifle calibers (albeit, inconclusive as to exactly which rifle calibers and ammunition).
The best approach to this concern is specification of door sets rated under SD-STD-01.01. An alternative option is employing independent door and lock assemblies rated UL 752 level 7+ or EN 1522 FB5+. Surelock McGill, for example, offers a number of lock assemblies and cylinder guards rated EN 1522 up to level FB7.[24]
For organizations without the budget and/or risk justification to equip safe rooms with door sets rated under ballistic resistance standards, the next best option is installing surface-mounted deadbolt locks on the inside of solid wooden or steel doors. Although most solid wooden and steel pedestrian doors are vulnerable to penetration by small arms, the door material will provide some reduction in bullet velocity and conceal location of the lock to reduce hit probability. Augmenting existing locks with bullet-resistant cylinder guards certified under UL 752 and/or EN 1522 is another possible enhancement. Conventional steel wrap-around door knob plates are not bullet-resistant, but may offer a marginal benefit by reducing projectile velocity. Additionally, bored locks may be preferred to mortise locks due to their smaller target size. As an additional concern regarding mortise locksets, wooden doors may critically weaken when struck repeatedly by gunfire in the location of the mortise pocket due to the thin layers of wood in this area.
Electrified Locks and Access Control Design
If a facility is employing/or planning to use electrified locks on potential safe room doors, careful consideration should be used in configuration of the access control system and hardware specification. Although access control systems offer great versatility in security design, they often suffer from vulnerabilities in real world application, which can be problematic during active shooter attacks.
In many buildings the author has assessed over the past several years, facilities were designed as large workspaces with few offices, storage rooms, or conference rooms suitable for use as safe rooms. In some of these facilities, permissions were broadly granted to employees through the facility’s access control system to allow convenient access to conference rooms and shared offices. During an attack by an insider adversary, doors with broadly applied access privileges will not provide useful protection. Likewise, if the access control system in the facility employs card readers and an outsider adversary recovers an access badge from a fallen employee, all doors with universal access will be compromised.
Another common problem relates to the fail-safe/secure configuration of electrified locking systems. Building and life safety codes universally require that egress doors equipped with electromagnetic locks ‘fail safe’ (unlocked) during fire alarms.[25] Although safe room doors in most situations will not be classified as egress doors, the author has discovered a number of facilities during his consulting activity where all access-controlled doors were universally configured to fail safe due to poor system design. In this situation, all fire alarm pull stations in the facility are ‘virtual master keys’ and would compromise most doors if someone activated a pull handle. This is a very real concern. In a number of previous attacks, fire alarms were manually activated by building occupants to alert others (e.g., 2013 Washington Navy Yard) or used by adversaries to deceptively herd victims outdoors for ambush (e.g., 1998 Westside Middle School, 2013 UCF, 2015 North Africa Hotel, etc.).[26][27]
In addition to fire alarms, electromagnetic locks without emergency power support fail safe automatically during electrical failures. Electromagnetic locks also fail safe by virtue of basic function if electrical lines are damaged (such as during an IED attack). Doors employing mechanical locksets and electric strikes configured to fail secure during power disruption are less vulnerable to compromise by electrical failure and fire alarms, but may be more vulnerable to forced entry than doors solely equipped with mechanical locks. Consequentially, CPNI in the United Kingdom specifically discourages use of electric strike plates on security doors.[28]
If designated safe rooms are already equipped with electrified locks, all aforementioned concerns can be mitigated by installing independent mechanical deadbolt locks for emergency use.
Windows
As a general rule, window and door glazing should be avoided in high risk situations or applications where designers seek ambitious delay goals. Although there are glazing products capable of high delay times, such systems are quite expensive by comparison to the price of wall construction and doors. In low-medium risk applications and situations where glazing is an unavoidable element of architectural aesthetics, windows should be designed to adequately resist intrusion. As described in part one of this article, adversaries most often focus penetration efforts on visually-obvious portals, and windows are often perceived as a vulnerable point for entry. Consequentially, the performance of glazing should be a top priority and may even exceed the importance of delay provided by barriers along less obvious intrusion paths such as walls, floors, and ceilings.
Window Dimensions (Unprotected Glass Windows)
In accordance with U.S. DoD recommendations, all unprotected windows on safe rooms should be 96 in2 (619 cm2) or smaller.[29] In addition the U.S. DoD guideline, we recommend that any unprotected glass windows or vision panels within arm’s reach (approx. 36″ or 91.5 cm) of door handles and locks have a width of no more than 1.5″ (3.8 cm).
Intrusion Resistance of Windows and Glazing
If window dimensions do not conform to the aforementioned guidelines, glass should be replaced or upgraded with intrusion-resistant materials. Tempered safety glass is generally only 4-5 times resistant to impact as annealed glass and provides minimal delay against forced intrusion. According to testing documented by Sandia, 0.25 inch tempered glass provides 3-9 seconds of delay against an intruder using a fire axe and the mean delay time for penetrating 1/8″ tempered glass with a hammer is 0.5 minutes.[30] Furthermore, impact testing documented by Sandia did not account for the fragility of tempered glass after first being penetrated by firearm projectile. In penetration tests Critical Intervention Services conducted of 1/4-inch tempered glass windows using several shots from a 9mm handgun prior to impact by hand, delay time was only 10 seconds.[31]
Some intrusion-resistant glazing options appropriate in low-medium risk applications include laminated glass, polycarbonate, and glass reinforced with properly attached anti-shatter film.
Laminated glass is a composite material constructed of two or more layers of glass bonded to a PVB or polycarbonate interlayer. According to Sandia’s test data, 1/4-inch laminated glass provides 18-54 seconds of delay against forced entry by fire axe and the mean delay time for penetrating 9/16-inch laminated security glass is approximately 1.5 minutes by hand tools.[32][33] Most glazing products tested and rated under forced entry standards UL 972 and EN 356 are constructed of laminated glass.
Polycarbonate is another option for intrusion-resistant windows. At thinner dimensions, polycarbonate provides decent impact resistance but comparable performance to tempered glass against fire axe attacks.[34] Polycarbonate truly distinguishes its benefit at thicknesses of 1/2-inch or greater. According to tests documented by the Nuclear Security Systems Directorate, 1/2-inch polycarbonate can delay hand tool penetration for up to two minutes.[35] Sandia cites 2-6 minutes of delay for penetration of polycarbonate by fire axe and sledgehammer.[36] Polycarbonate is relatively inexpensive and can be purchased as sheets and cut to dimensions as needed. The main disadvantages of polycarbonate are its limited resistance to scratch damage and susceptibility to discoloration and degradation from UV exposure.[37] Some tests also suggest polycarbonate may be vulnerable to fragmentation and shatter critically when penetrated by 12-gauge shotgun.[38]
In low risk situations or circumstances where budget does not permit replacing existing glazing, anti-shatter film properly attached and anchored to tempered or annealed glass may be a cost-effective alternative. Regretfully, Sandia never published data on the penetration times of film-reinforced glazing. In 2015, CIS participated in a series of tests of 1/4-inch tempered glass windows with mechanically-attached 11 mil window film. The tests involved penetration by firearm followed by impact (kicking and rifle buttstock). The delay times ranged from 62 to 94 seconds and deviated according to the aggression of our penetration tester.[39] Although the sample size was small, the CIS test times at least provide a reasonable expectation for performance of window film during active shooter attacks. If anti-shatter film is chosen as an upgrade, specifications should require mechanical or cement bond frame attachment.
To facilitate performance in safe room designs with delay time goals over 60 seconds, it is recommended that designers use glazing products rated for intrusion resistance under ASTM F1233-08, EN 356, and EN 1627. If the threat definition identifies firearm penetration and buttstock impact as the primary methods of entry, reasonable specifications include ASTM F1233-08 Class 2+ Body Passage, EN 356 P6B+, and EN 1627 RC4+. UL 972 is another option, but in the author’s opinion should only be specified in low-medium risk applications. See Part 4 of this series for a survey of window protection standards and their relevant merits and disadvantages in safe room design.
Ballistic Resistance and Windows
For ballistic resistance, specifications for protection against military small arms include EN 1063 BR5-BR7, UL 752 Level 7-9, and ASTM F1233-08 R1-R4AP.
Ceilings and Floors
Although penetration through ceilings or floors is possible, such paths of entry are least likely considering typical construction characteristics and adversary behavior as witnessed during previous armed attacks. However, in high risk design applications, floors and ceilings should provide balanced protection according to the safe room’s specified delay time objectives. For this purpose, Sandia’s Barrier Technology Handbook provides a good survey of penetration times for a wide range of ceiling and floor construction variations.[40]


























Recent Comments