
Facility Preparation for Active Shooter Attacks: Key Objectives (Pt. 3)
In Part 1 of this series, we discussed how the integration of detection, delay, and response functions influences the overall performance of physical security. In security designs aimed at the protection of inanimate assets (such as theft prevention and anti-sabotage situations), hardware components and physical construction (e.g., anti-personnel barriers, alarm systems, CCTV, etc.) are often the primary elements facilitating detection and delay. However, in the case of active shooter attacks, anticipating the actions of facility occupants is critical in designing a successful system.
Most organizations concerned about active shooter attacks have adopted the US Department of Homeland Security’s classic ‘Run-Hide-Fight’ doctrine as the basis for designing facility emergency action plans and training employees. This simplified response guidance is presented as a prioritized list of preferred protective responses when an active shooter attack is recognized. “Run,” for instance, should always be the first option when the opportunity is present. If “Run” is not possible, then “Hide” is the next prioritized option.
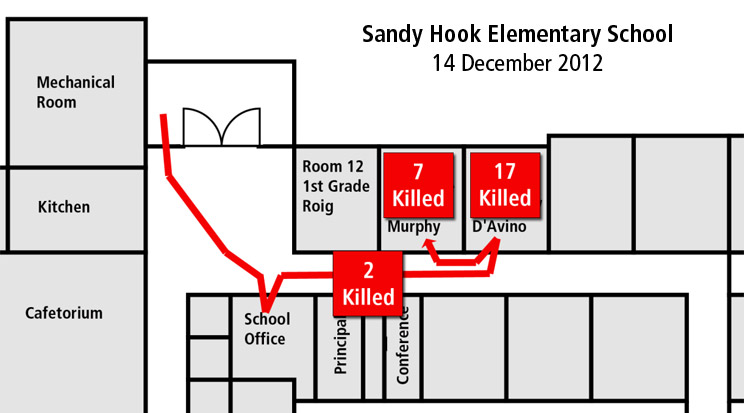
Although “Run” is generally the most preferred response, there are situations where attempting escape may be more dangerous than simply remaining in place. A good example is a multi-story building when an attack is launched at ground level. Rarely during attacks do people in the “hot zone” have accurate and real-time knowledge of the attacker’s location and safe routes of escape. In this situation, trying to evacuate through lower levels of the building where possible massacre is in progress may be far more dangerous than barricading in a nearby safe location.
To ensure best performance during armed attacks, facilities should be designed or upgraded to support these response actions and proactively address common challenges faced by people during life-threatening events.
Physical Security and Active Shooters: Key Objectives
The following points summarize key measures for protecting facility occupants during active shooter events.
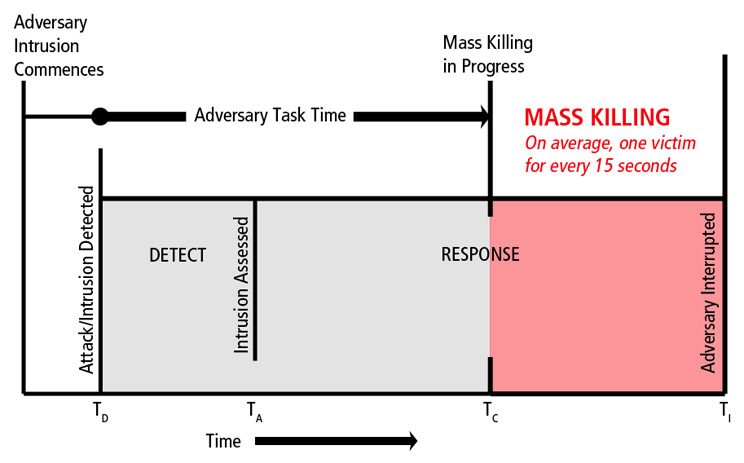
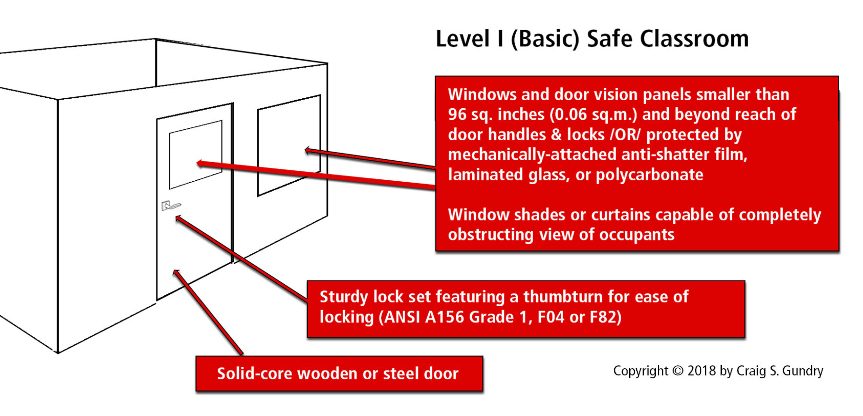
Delay the attacker’s ingress into populated areas to permit time for critical alerts, escape and refuge actions, and deployment of the response force. (DELAY)
Protective layers should be designed to delay adversary movement into populated areas. If the attacker is an ‘outsider,’ this includes exterior barrier layers (e.g., facade glazing, doors, locks, etc.) and delay measures at entry points and public reception areas (e.g., lobbies, etc.). Additional protective layers securing work suites and high-valued assets (e.g., executive offices, etc.) should be used to frustrate adversary ingress further and provide critical delay against movement by ‘insider’ adversaries already located inside the building.
Expedite detection and assessment of the threat. (DETECTION)
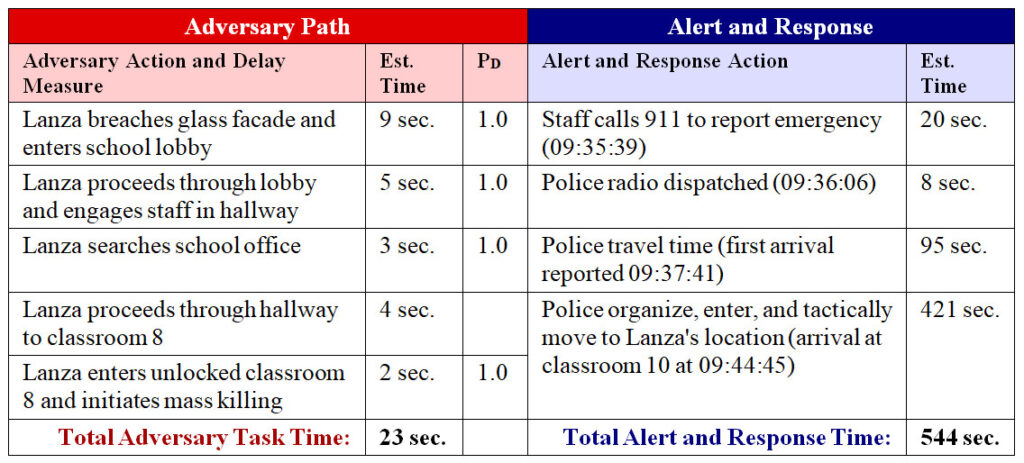
As discussed in Part 1 of this series, time is critical during active shooter events and every measure that expedites detection of the attack and deployment of an armed response force is critical in mitigating consequences. Measures that expedite event notification to security or authorities, such as panic alarms or gunshot detection systems, can greatly reduce the typical reporting times normally encountered by relying on witnesses to call an emergency number by telephone.
Rapidly and reliably alert all facility occupants. (DETECTION)
A critical part of effective response during active shooter events is fast and reliable alert to expedite protective actions by employees. Critical alerts should ideally be issued by audible means (public address) for the benefit of all facility occupants, and where feasible, followed by a redundant mass notification system (MNS) message for those who may not have heard the initial announcement. When important developments occur, updates can be issued to employees as follow up messages.
Facilitate easy and rapid evacuation/escape by employees and facility guests. (DELAY)
For employees located outdoors, ground level, or in building locations without safe refuge options, escape (DHS’ term ‘Run’) is the primary response. Escape routes should be abundantly available, easy to locate, and permit fast and unobstructed egress to safe locations away from the facility.
Provide safe refuge options for employees and facility guests unable to safely evacuate or who are unaware of the threat’s location. (DELAY)
One of the most basic facility preparations is ensuring adequate availability of safe rooms for people to take refuge if escape is not feasible. For this purpose, rooms should be abundantly available throughout the facility capable of providing adequate delay against forced entry considering the methods and tools likely to be employed by attackers.
Expedite the intervention of a response force capable of neutralizing an armed adversary. (RESPONSE)
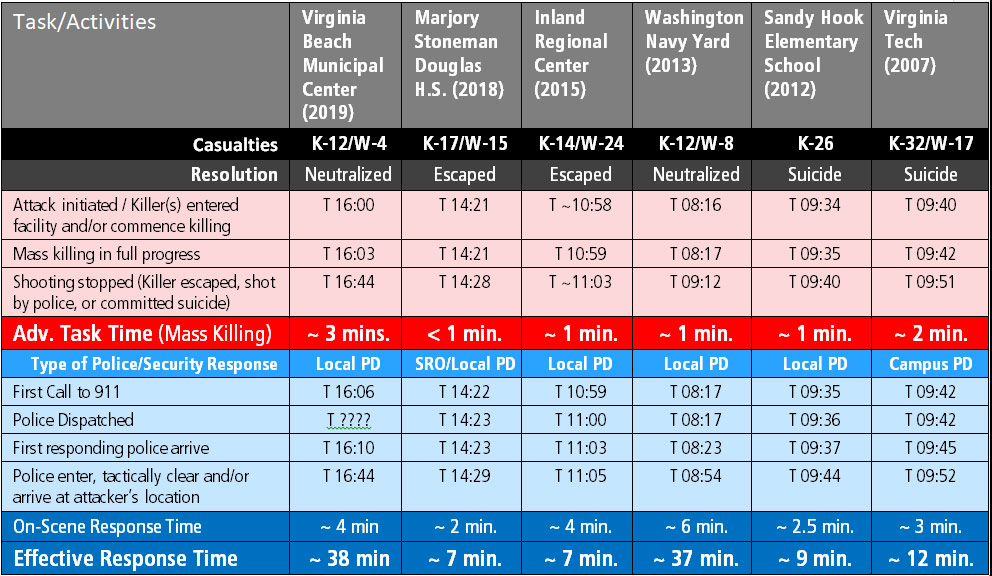
Although many active shooter attacks terminate in suicide before the intervention of police or security forces, the speed at which security or police arrive and locate the adversary has a major impact on consequences of the event.
In an ideal scenario, police or armed security officers would be assigned to reliably ensure fast response times. If an organization cannot implement an on-site armed response capability, additional measures should be used to expedite the effective response of local police. Some examples include marking buildings on multi-building campuses with distinctive signage to ease location, establishing procedures for orienting and directing law enforcement officers as they arrive on scene, and preparations for providing building keys, access control badges, and floor plans to facilitate unimpeded movement by police.
Ensure employees are prepared to respond safely and without direction.
Even the best designed plans and facility preparations will fail if employees are unprepared to take independent action for their self-preservation during active shooter events. As detailed further in Part 4 of this series, the effects of the sympathetic nervous system during high stress events and lack of situational awareness can have a debilitating effect on employee response and even lead to dangerous actions. The first step in combating this problem is training employees in emergency response procedures.
The Department of Homeland Security and various municipalities throughout the US have produced short videos useful for this purpose. It is also recommended that training include instructor-led discussion about facility-specific measures for contacting security or police, location of suitable safe rooms inside the facility, special egress considerations (e.g., feasibility of roof access, etc.), communications systems, and location of medical kits.
In the next part of this series, we’ll explore common challenges and unique circumstances that often influence how these principles are best applied in different facility situations.

Craig Gundry
Copyright © 2020 by Craig S. Gundry, PSP, cATO
CIS consultants offer a range of services to assist organizations in managing risks of active shooter violence.
Contact us for more information.














Recent Comments