
Physical Security Design and The Active Shooter (Pt. 1)
When many people think of physical security, the first ideas that come to mind are things like locks, alarm systems, screening with metal detectors, CCTV, etc.—hardware components or procedures. Although these elements play a role in physical security, they have no value outside the context of the overarching system design.
In the context of active assailant attacks, performance-based physical security design integrates Detection, Delay, and Response elements in a manner that mathematically reconciles the time required for an adversary to commence mass killing and the time required for detection and response by security or police.
Fundamentally, physical security design is a mathematics problem defined by several key times and probabilities. The main performance metric of a Physical Protection System (PPS) design is its Probability of Interruption, defined as the probability that an adversary will be detected and intercepted by a response force before he/she can complete their objective.[1] The most important elements determining the Probability of Interruption are the Adversary Task Time (total time required for an adversary to enter a facility and access their target) and response force time. If the total time for detection, assessment, communications, and response force intervention is longer than the adversary task time, the system will fail. Specific elements alone (such as having an access control system or CCTV cameras) mean nothing outside the context of the overall system design. Individual PPS elements must work together integrally to reconcile these key times or the adversary will succeed.
In the context of active shooter events, detection usually is the result of visual or audible observation when the attack commences. Detection may also result from an alarm signal generated by forced entry into secured spaces or gunshot detection systems. The Time of Detection during an attack is represented in figure 1 as TD.
The time the report is received by authorities and/or assessed by a security control room for deployment of on-site armed officers is represented in the diagram as TA (Time of Assessment).
After the 911/112 center or security control room is alerted, the response force is subsequently dispatched to intercept and neutralize the adversary. This is represented in the following diagram as the Time of Interruption (TI).
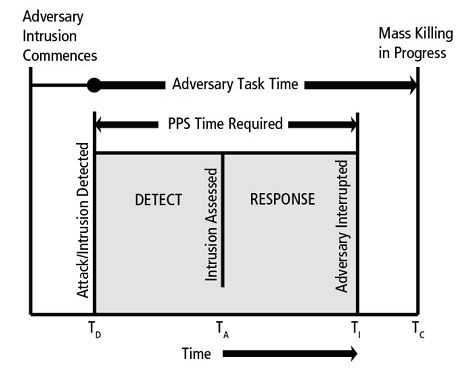
While the alert and response force deployment is in progress, the adversary advances through barriers and distance to access targets and initiate mass killing. The time mass killing is in progress is represented in the previous diagram as Time of Completion (TC). The Adversary Task Time is the cumulative time between the Time of Detection and the Time of Completion. If the Time of Interruption is before the Time of Completion, the Physical Protection System (PPS) is successful in its function of preventing mass killing.
In most previous active shooter attacks, deficiencies in one or more key functional elements (Detection, Delay, or Response) result in a situation where mass killing (TC) initiates before the response force intervenes (TI).
Based on data yielded during several studies of active shooter attacks, the consequences of the difference in time between commencement of mass killing and response force intervention (TC versus TI) can be estimated as one casualty per 15 seconds.[2]
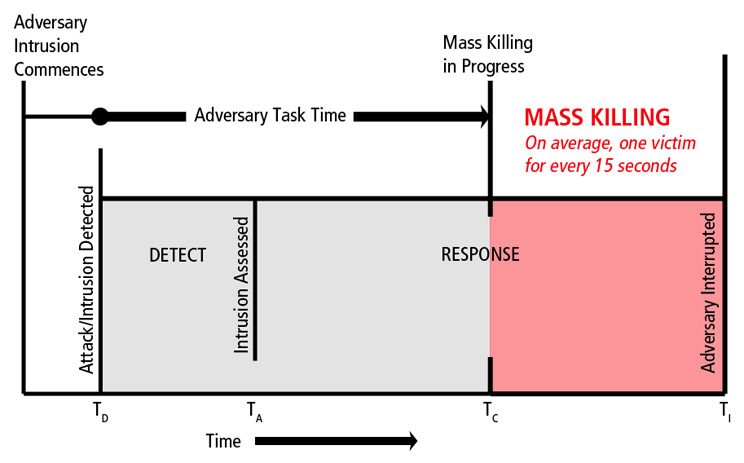
Although the ideal objective of PPS design is to interrupt mass killing before it commences, real world conditions often limit the possibility of achieving a high Probability of Interruption. This type of situation is often common in ‘soft target’ facilities due to the need for unobstructed public access and facilities reliant on the unpredictable response times of off-site police. Other real world challenges such as cultural expectations, branding, and budget boundaries often limit the feasibility of implementing ideal physical security measures. And if an attack is launched by an insider adversary (e.g., employee, student, etc.) already inside the facility, physical protection elements at outer protective layers (e.g., perimeter, building envelope, entrances, etc.) will have little or no benefit.
Nevertheless, all measures that increase Adversary Task Time and expedite response time have a direct benefit in reducing potential casualties by narrowing the gap between TC and TI.
Sandy Hook Elementary School, 14 December 2012: Case Study of Performance-Based Physical Security Principles in Practical Application
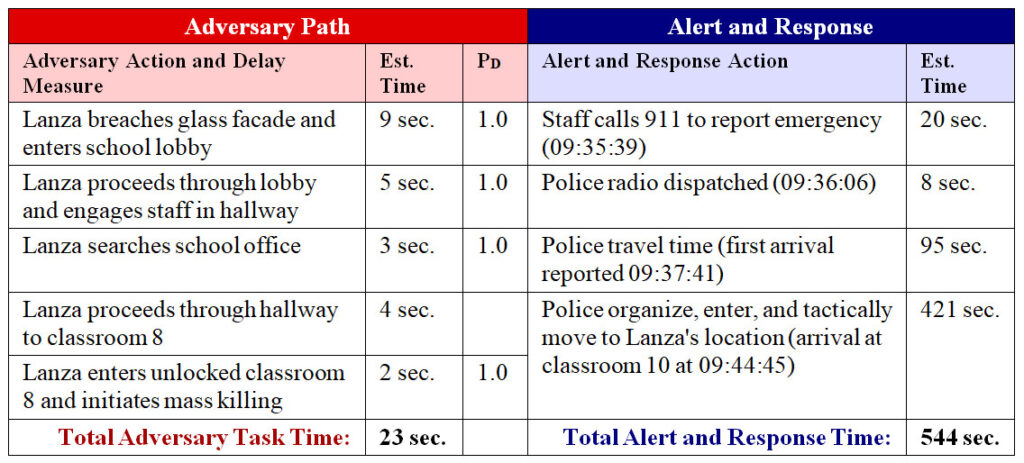
At approximately 09:34, Adam Lanza used an AR-15 rifle to shoot through a tempered glass window adjacent to the school’s locked entrance doors and passed into the lobby.[3]
After killing the school principal and a school psychologist and injuring two other staff members who entered the hallway to investigate, Lanza entered the school office. Meanwhile, staff members concealed inside the school office and nearby rooms initiated the first calls to 911. Staff located throughout the building were alerted when the ‘all-call’ button on a telephone was accidentally activated during a 911 call.
After finding no targets in the office, Lanza returned to the hallway and proceeded into the unlocked door of first grade classroom 8 where mass murder commenced (approx. 09:36).[4] In less than two minutes, Lanza killed two teachers and fifteen students.
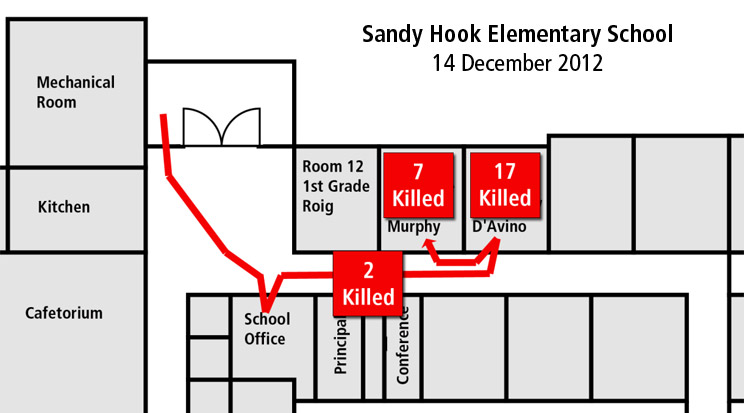
As the attack in classroom 8 was in progress, teacher Victoria Soto and a teaching assistant in classroom 10 attempted to conceal children in cabinets and a closet.
After exhausting targets in classroom 8, Lanza proceeded into classroom 10 and killed Ms. Soto, assistant Anne Murphy, and five children. Although the exact reason Ms. Soto did not lock the door to classroom 10 is unknown, all classrooms at Sandy Hook Elementary School featured ANSI/BHMA “classroom-function” (mortise F05 and bored F84) locks which can only be locked with a key from the hallway-side of the door.
The tragedy ended in classroom 10 when Lanza committed suicide at 09:40 while police were preparing for entry into the building.
As common in U.S. primary schools, Sandy Hook Elementary School relied on off-site police as their response force during emergency events. Response was first initiated at 09:35 when a staff member called 911 to report the crisis. At 09:36, an alert was broadcast by radio and police units were dispatched to the school. The first police unit arrived at 09:39, followed immediately by two other units. After assessing the scene and planning a point of entry, the officers organized into a contact team and made entry into the school at 09:44.
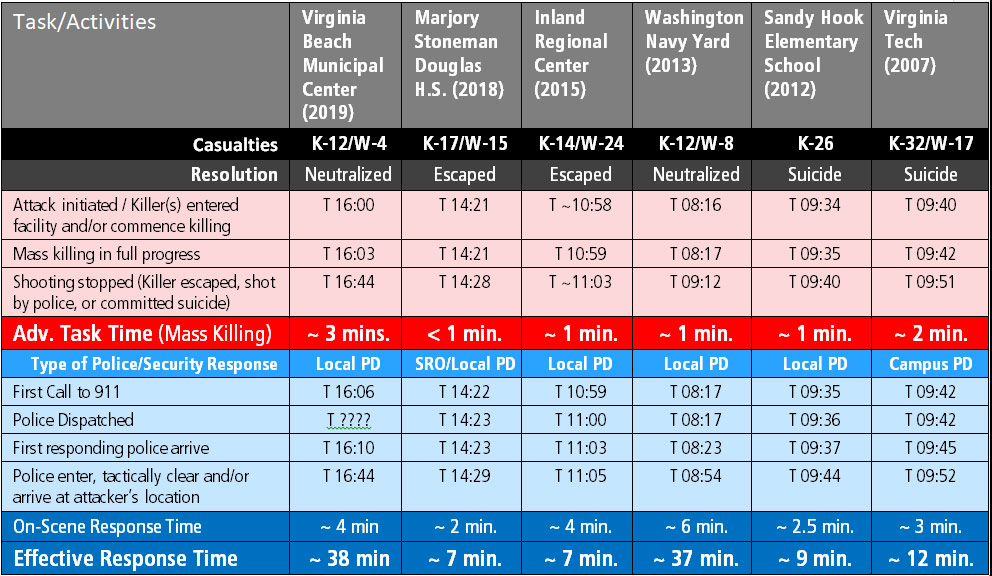
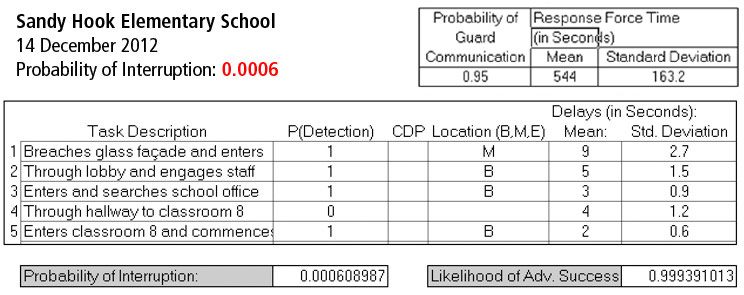
In the context of physical protection system performance, the adversary task time (time between when Lanza’s entry commenced and mass killing was in progress) at Sandy Hook Elementary School was approximately 23 seconds. The time between detection of the attack and on-site arrival of police was slightly less than three minutes. However, there was an additional 5-6 minutes of time as officers assessed the situation and organized before making entry and effectively moving indoors to neutralize the killer. When assessing incidents involving response by off-site police, arrival time at the scene is irrelevant. What matters is the time ending when police arrive at the immediate location of the adversary ready to neutralize the threat. This describes the contrast between On-Site Response Time and Effective Response Time. At Sandy Hook Elementary School, the Effective Response Time was approximately nine minutes.
As illustrated in the following table, the variation between Adversary Task Time and Effective Response Time witnessed at Sandy Hook Elementary School has been historically common during active assailant attacks. In each of the six events documented below, mass killing was in full progress within 1-3 minutes of the time the attacker entered the building or shot the first victim. By comparison, the Effective Response Times ranged between 7 and 38 minutes, with most events ending prior to intervention by police when the attacker(s) escaped or committed suicide.
Mitigating the consequences of active shooter attacks through better physical security design and integration
In the Newtown tragedy, PPS failure was largely the result of inadequate delay in relation to the time required for response by off-site police. When the attack is analyzed using Sandia’s Estimate of Adversary Sequence Interruption (EASI) Model, the original PPS at Sandy Hook Elementary School would have had a Probability of Interruption of 0.0006 (Very Low).
In the case of Sandy Hook Elementary School, there are a number of measures that could have improved overall system performance.
Upgrade the facade with intrusion-resistant glazing. Adam Lanza entered the building by bypassing the locked entrance doors and shooting a hole through the adjacent tempered glass window. He then struck the fractured window and climbed through the breach. Tempered safety glass is generally only 4-5 times resistant to impact as annealed glass and provides minimal delay against forced intrusion. According to testing documented by Sandia National Laboratories, 0.25 inch tempered glass provides 3-9 seconds of delay against an intruder using a fire axe and the mean delay time for penetrating 1/8″ tempered glass with a hammer is 0.5 minutes.[5] However, impact testing documented by Sandia did not account for the fragility of a tempered glass specimen after first being penetrated by firearm projectile. In penetration tests Critical Intervention Services conducted of 1/4-inch tempered glass windows using several shots from a 9mm handgun to penetrate glazing prior to impact by hand, delay time was only 10 seconds.[6]
Upgrading facade glazing with the use of mechanically-attached anti-shatter film could have improved delay time at the exterior protective layer by 60-90 seconds.[7]
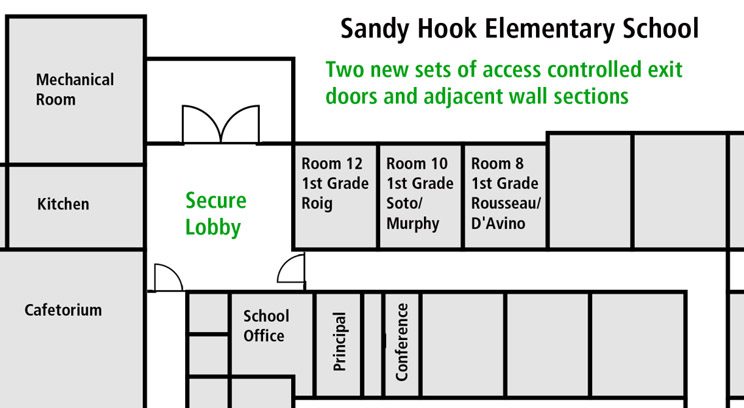
Replace “classroom-function” locks on school doors with locks featuring an interior button or thumbturn. All classroom doors inside Sandy Hook Elementary were equipped with ANSI “classroom-function” locks (mortise F05 and bored F84). These are perhaps the worst choice of locks possible for lockdown purposes during active shooter events. As witnessed in a number of attacks, doors equipped with classroom-function locks often remain unlocked due to difficulty locating or manipulating keys under stress. In addition to Sandy Hook classroom 10, another incident where this situation clearly contributed to unnecessary casualties was the 2007 Virginia Tech Norris Hall attack.[9] In these two events alone, 26 students and faculty were killed and 24 wounded specifically because the doors to classrooms could not be reliably secured.
Ideal specifications for door locks would be ANSI/BHMA A156 Grade 1 with an ANSI lock code of F04 or F82.[10] Mechanical locks rated ANSI/BHMA Grade 1 have been successfully evaluated under a variety of static force and torque tests. Locks coded as F04 and F82 feature buttons or thumbturns to facilitate ease of locking under stress.
Although there are no empirical sources citing tested forced entry times against ANSI/BHMA A156 Grade 1 rated locks, it is estimated that a committed adversary using impact force with no additional tools could penetrate improved locks in approximately 90-110 seconds.
Replace door vision panels with intrusion-resistant glazing. During the attack at Sandy Hook Elementary, Adam Lanza was able to enter classrooms 8 and 10 directly through unlocked doors. If these classrooms were secured, the tempered glass vision panels on all classroom doors could have been easily breached to facilitate entry in less than 10 seconds.
An effective approach to physical security specification would ensure that all barriers composing the classroom protective layer are composed of materials with similar delay time values. This could be accomplished by ensuring that vision panels are no wider than 1.5″ (3.8 cm) or constructed of intrusion-resistant glazing such as laminated glass, polycarbonate, or reinforced with anti-shatter film.
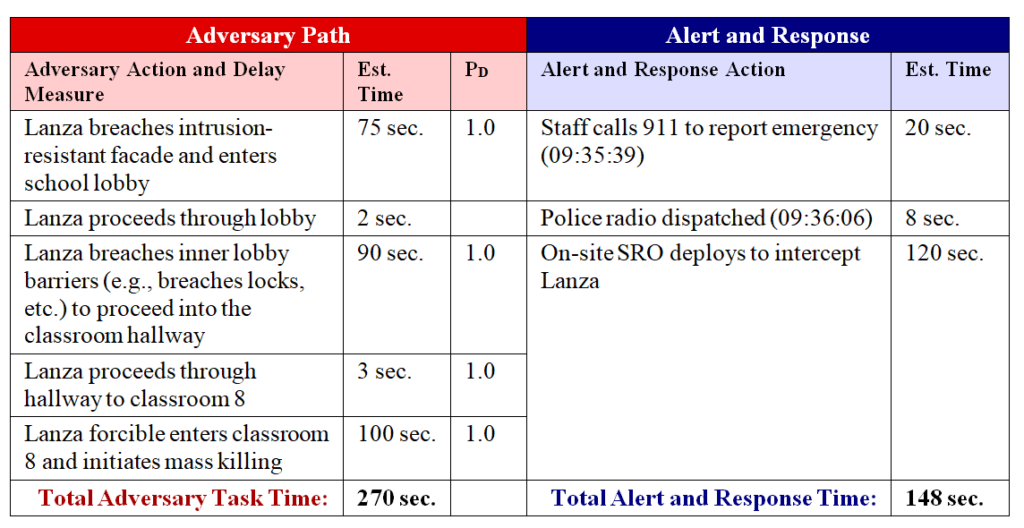
If the aforementioned barrier improvements were employed in the PPS design at Sandy Hook Elementary School, Adam Lanza’s access into occupied classrooms would have been delayed by an additional 162-312 seconds. This would have improved the overall performance of the PPS by potentially increasing the Adversary Task Time to 185-335 seconds before mass killing was in progress. Although this is a significant improvement from the original Adversary Task Time (est. 23 seconds), 335 seconds is still less than the estimated response time of police during the original event (est. 544 seconds).
In many cases, accomplishing the performance-based objective of interrupting an active shooter before mass killing commences requires a combined approach aimed at both increasing delay time and decreasing response force time. In the case of Sandy Hook Elementary School, decreased response time could have been facilitated by the use of gunshot detection technology or duress alarms, improved communications procedures, and similar improvements. Any measure that decreases alert notification and response times has a beneficial impact on system performance. Even if enhancements only reduce response time by 10 or 15 seconds, such improvements have the theoretical benefit of reducing casualties by one victim per fifteen seconds of decreased response time.
In the situation of Sandy Hook Elementary School, the greatest improvement could have resulted from having an on-site response force (e.g., armed school resource officer) capable of reliably responding anywhere on the school campus within 120 seconds of alert.[11] If this measure were implemented, the total estimated alert and response time could have been improved to 147-157 seconds. When compared to the increased Adversary Task Time of 206-316 seconds, the improved PPS design would have likely resulted in interruption before mass homicide commenced. When analyzed using Sandia’s Estimate of Adversary Sequence Interruption (EASI) Model, the improved PPS would have resulted in a Probability of Interruption of 0.87 (Very High).
The following table and spreadsheet models the PPS improvements described in this article to demonstrate how performance-based physical security design can influence the outcome of armed attacks.
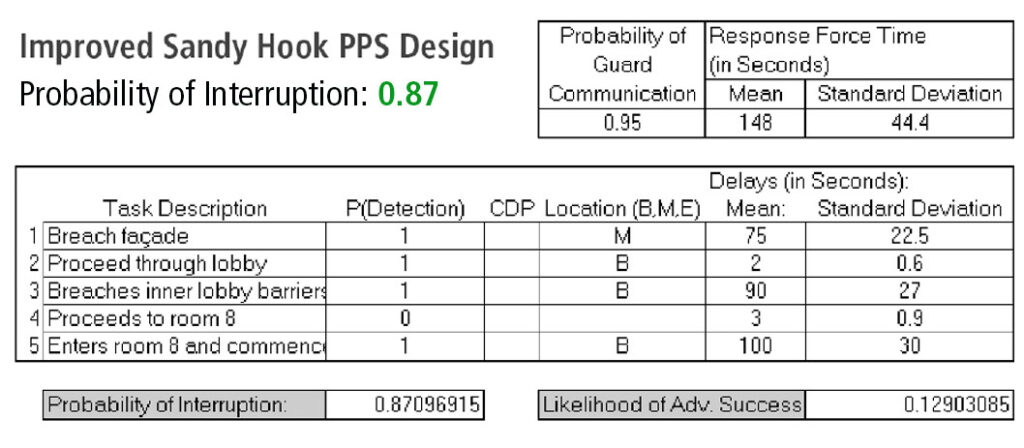
Threat Characteristics and Physical Security Performance
The delay time expectations of physical barriers cited in this article were based on the weaponry and methods of entry employed by Adam Lanza at Sandy Hook Elementary School. If Lanza had employed different tools or methods, the delay time of barriers would have correspondingly been different. The same principle is true for bullet-resistant barriers. The ballistic resistance of materials is directly relative to the caliber and type of ammunition used by an adversary.
To ensure a security design performs as expected, it is first necessary to establish a definition of the adversary’s likely capabilities and tactics. In Part 2 of this series, we’ll continue this discussion by exploring trends in the behavior of attackers, threat capabilities and methods, and approaches to developing a Design Basis Threat (DBT) suitable for security planning.
[1] Garcia, Mary Lynn. Design and Evaluation of Physical Protection Systems. Burlington, MA: Elsevier Butterworth-Heinemann, 2007.
[2] Anklam, Charles, Adam Kirby, Filipo Sharevski, and J. Eric Dietz. “Mitigating Active Shooter Impact: Analysis for Policy Options Based on Agent/computer-based Modeling.” Journal of Emergency Management 13.3 (2014): 201-16.
[3] Sedensky, Stephen J. Report of the State’s Attorney for the Judicial District of Danbury on the shootings at Sandy Hook Elementary School and 36 Yogananda Street, Newtown, Connecticut on December 14, 2012. Danbury, Ct.: Office of the State’s Attorney. Judicial District of Danbury, 2013. Print.
[4] Time estimated based on witness event descriptions and assessment of time required to walk through the school office and down the corridor to classroom 8.
[5] Barrier Technology Handbook, SAND77-0777. Sandia Laboratories, 1978.
[6] Critical Intervention Services assisted a window film manufacturer in 2015 in conducting a series of timed penetration tests of 1/4-inch tempered glass windows with mechanically-attached 11 mil window film. The tests involved penetration by firearm followed by impact (kicking and rifle buttstock). The delay times ranged from 62 to 94 seconds and deviated according to the aggression of our penetration tester.
[7] Ibid.
[8] Gundry, Craig S. “Analysis of 20 Marauding Terrorist Firearm Attacks.” Preparing for Active Shooter Events. ASIS Europe 2017, 30 Mar. 2017, Milan, Italy.
[9] Mass Shootings at Virginia Tech. April 16, 2007. Report of the Review Panel. Virginia Tech Review Panel. August 2007. pp.13.
[10] ANSI/BHMA A156.13, Mortise Locks and Latches. Builders Hardware Manufacturers Association (BHMA), New York, NY, 2011.
[11] CIS Guardian SafeSchool Program® standards define a performance benchmark of 120 seconds as the maximum time for acceptable response by on-site officers. However, achieving this type of response time in many facilities requires careful consideration of facility geography, communications systems, access obstructions, and officer capabilities (e.g., training, physical conditioning, etc.).

Craig Gundry
Copyright © 2020 by Craig S. Gundry, PSP, cATO
CIS consultants offer a range of services to assist organizations in managing risks of active shooter violence.
Contact us for more information.






Recent Comments